IGNOU Assignment MCS 42 Solution - Discuss the implementation of Kerberos mechanism.
Written On : 12-Apr-2020
Author : Neha Dubey

Looking for solved IGNOU assignments of MCS 42? Check out the answer of IGNOU MCS 42 assignment question - Discuss the implementation of Kerberos mechanism here.
Discuss the implementation of the Kerberos mechanism is Question No. 12 of IGNOU MCS 42 assignment 2020. Here is the solution/answer for the given IGNOU assignment question.
IGNOU MCS 42 Assignment Solution - Q.12 Discuss the implementation of Kerberos mechanism
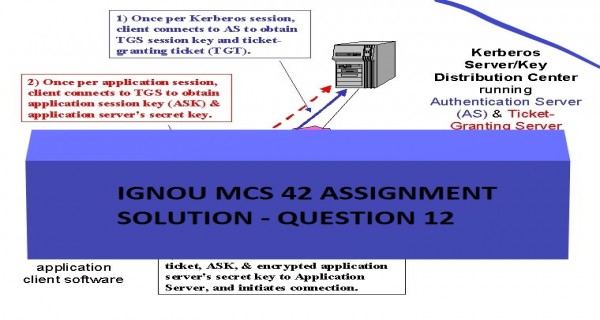
Kerberos (as shown in the below Figure) employs a client/server architecture and provides user-to-server authentication rather than host-to-host authentication. In this model, security and authentication will be based on a secret key technology where every host on the network has its own secret key. It would clearly be unmanageable if every host had to know the keys of all other hosts so, a secure, trusted host somewhere on the network, known as a Key Distribution Centre (KDC), knows the keys of all the hosts (or at least some of the hosts within a portion of the network, called a realm). In this way, when a new node is brought online, only the KDC and the new node need to be configured with the node’s key; keys can be distributed physically or by some other secure means.
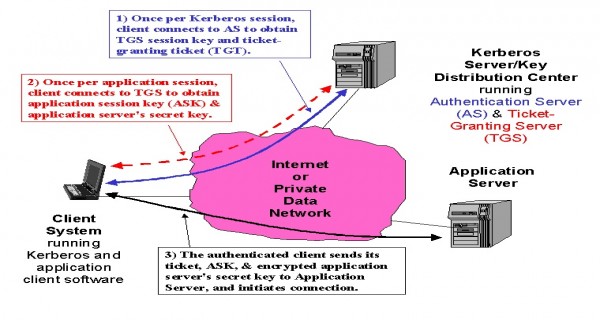
The Kerberos Server/KDC has two main functions (Figure), known as the Authentication Server (AS) and Ticket-Granting Server (TGS). The steps in establishing an authenticated session between an application client and the application server are:
- The Kerberos client software establishes a connection with the Kerberos server’s AS function. The AS firstly authenticates that the client is who it purports to be. The AS then provides the client with a secret key for this login session (the TGS session key) and a ticket-granting ticket (TGT), which gives the client permission to talk to the TGS. The ticket has a finite lifetime so that the authentication process is repeated periodically.
- The client now communicates with the TGS to obtain the Application Server’s key so that it (the client) can establish a connection with the service it wants. The client supplies the TGS with the TGS session key and TGT; the TGS responds with an application session key (ASK) and an encrypted form of the Application Server’s secret key; this secret key is never sent on the network in any other form.
- The client has now authenticated itself and can prove its identity to the Application Server by supplying the Kerberos ticket, application session key, and encrypted Application Server secret key. The Application Server responds with similarly encrypted information to authenticate itself to the client. At this point, the client can initiate the intended service requests (e.g., Telnet, FTP, HTTP, or e-commerce transaction session establishment).
So here was the solved IGNOU MCS 42 assignment question No. 12 i.e., Discuss the implementation of Kerberos mechanism.
How to Prepare for AFCAT Exam
Comments
No comments received yet. Be first to comment.
Please sign in to comment.